31 | Add to Reading ListSource URL: junior-fellows.gi.deLanguage: English - Date: 2016-05-17 12:18:49
|
|---|
32 | Add to Reading ListSource URL: www.rosequarter.comLanguage: English - Date: 2016-07-01 14:39:58
|
|---|
33 | Add to Reading ListSource URL: www.surveon.comLanguage: English - Date: 2014-09-30 05:38:09
|
|---|
34 | Add to Reading ListSource URL: conference.htcias.comLanguage: English - Date: 2016-08-02 13:09:20
|
|---|
35 | Add to Reading ListSource URL: flttrack.fltplan.comLanguage: English - Date: 2016-03-25 11:27:07
|
|---|
36 | Add to Reading ListSource URL: www.cs.columbia.eduLanguage: English - Date: 2016-06-07 13:58:45
|
|---|
37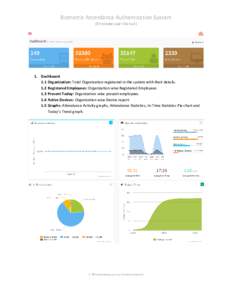 | Add to Reading ListSource URL: surveyofindia.attendance.gov.inLanguage: English - Date: 2015-02-20 06:43:35
|
|---|
38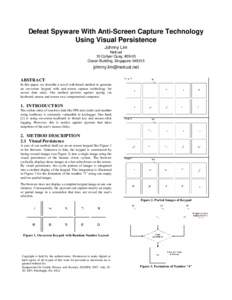 | Add to Reading ListSource URL: cups.cs.cmu.eduLanguage: English - Date: 2007-06-22 15:47:38
|
|---|
39 | Add to Reading ListSource URL: homeland.house.govLanguage: English - Date: 2016-07-05 08:45:24
|
|---|
40 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2015-08-24 18:12:50
|
|---|